With an increasing amount of cyber attacks around the globe it becomes clear that cybersecurity needs to be taken seriously by CEOs of small and large companies alike.
The PwC Cybersecurity Day on October 24 provided many valuable insights from the latest international developments in cybersecurity and privacy. For everyone who was not able to attend the event, we’re sharing some of those insights now within this article. More info can also be found directly on the PwC blog.
First of all: Doubting the fact that your business will be attacked is futile. We’ve gotten to the point when the most appropriate and helpful question is when it will happen. This sentence arguably states the obvious, but redundancy is odiously necessary especially when 44% of the 9,500 executives in 122 countries surveyed by the 2018 GSISS say they do not have an overall information security strategy.
As a matter of fact, cyber attacks are increasing, and the consequences can be significant or even dramatic for any organisation. The digital transformation a large majority of organisations are going through—with the adoption of artificial intelligence, robotic process automation, the internet of things, for instance—is almost an unavoidable step for business sustainability and competitiveness but, at the same time, makes the need for a sound security strategy even more urgent.
There is still more than one third (37%) of financial services worldwide that acknowledge not including cyber and privacy management in their digital transformation, “fully from the start”.
Today’s CEOs have no choice but to take an active role in the business security strategy in a broad sense. That encompasses understanding what information security, cybersecurity and data security actions are being put in place but, more importantly, setting the right cybersecurity governance that allows for clear decision making and rapid action deployment to manage emerging cyber risks in an increasingly complex digital society.
Businesses have to build the resilience needed to withstand disruptive cyberattacks. To understand the needs, risks and measures of cybersecurity, CEOs want to step in the shoes of the CISO (Chief Information Security Officer), and CISOs need a clear access to the CEO, prompt and direct.
First things first. The C-suite is enlarging. Back in the late 90s the CIO (Chief Information Officer) joined the “classical” chiefs, the CFO, COO, and the CEO. There are even more newcomers joining the table now, like the CSO (Chief Sustainability Officer), for instance. And, there is the CISO.
With an increasing number of people in the C-Suite, how can the CISO’s voice get louder and properly understood? To further complicate the equation, let’s bring in another professional whose role is gaining traction in the business realm, especially in Europe, the DPO or Data Protection Officer. Are the CISO and the DPO intrinsically tied or, on the contrary, they overlap and are doomed to a conflicting relation?
This article is about building suitable communication and decision-making mechanisms among the CEO, CISO and the DPO that allow the latter two to plan for managing cybersecurity and data privacy, adapt strategies when necessary and respond quickly to a breach, data leak or any other emergency.
After all, without the right team in place, governance rules and clear management procedures, handling risks around security, privacy and ethics becomes a steeper climb.
How cybersecurity, data privacy and data protection converge
We can have security without privacy, but not vice versa. Without security, privacy is unattainable, an impossible ambition. In principle, data privacy and, more precisely, the protection of it, require security work.
Security and data privacy are like the Yin and Yang, the Chinese philosophy’s ancient dualism concept. Inseparable, they are opposite but complementary. Professionals responsible for them within a business aren’t exempted from having conflicts sometimes, but they are better when interacting with each other.
Data can be analog—stored in physical files—or digital. When the data to be kept safe and protected from unauthorised access lives in the digital realm, we talk about cybersecurity.
Some people use cybersecurity and data privacy interchangeably, but there are clear differences that any business wants to get right to put together a holistic security strategy.
Let’s get a little bit academic to understand these differences. Data privacy is about how data is collected, used, stored and shared. It includes personal data and, at business level, proprietary information such as trade secrets, staff and internal processes. Data security uses physical and logical mechanisms to protect information from cyberattacks and accidental (data leak) or intentional data losses (data breach). Cybersecurity, more vast as a field, fights cybercrime, cyber frauds and also data-security related attacks.
The GDPR has been precisely conceived to regulate data privacy matters in Europe, focusing on personal data. Its primary purpose is to increase privacy and extend data rights for EU residents and help them understand how their personal data is used.
Concepts, nevertheless, are neither set in stone nor subject to management issues or the lack of governance. People are.
The challenge, then, is for the CISO, the CIO and the DPO to position themselves properly in the business, to interact between them following clear procedures, and to access the board, and the CEO principally, to make timely decisions for an agile and resilient security strategy in all fronts.
Embracing cyber-resilience
The approach to the security of business information systems is taking a turn. They call it cyber-resilience and there are numerous definitions. Whichever you prefer, all of them share the same underlying fact: no business or organisation is 100% immune to cyberattacks. Yes, prevention will always be an important slice of the security strategy pie, but businesses want to develop the ability to resist or quickly recover from cyber attacks that want to disturb business operations.
When being cyber-resilient, the risk approach is more global, allowing for “absorbing” threats earlier and timely in the interests of the business and its customers. Ultimately, it helps build trust because it allows organisations to deliver the intended outcome at every moment.
However, for “earlier” and “quickly” to be more than adverbs in a well-written sentence, businesses want agile decision-making and clear governance for cybersecurity and data protection to be resilient and adaptable.
There isn’t a firewall, encryption system, antivirus software or network that can fight a lack of management support to embed cybersecurity as an organisation priority or cumbersome governance that impedes timely action.
Successful cybersecurity is, ultimately, about human willingness, accountability and the distribution of power in the organisation.
The information security steering committee
Information security, cybersecurity, data security, all of them are require investment. That, to many, is a burden particularly when these matters aren’t a business priority yet, but things are changing. “Whereas sufficient investment in cybersecurity capacity and personnel was seen as a necessary evil a few years ago, today it is a strategic imperative,” stated Joerg Asma, PwC Germany’ cybersecurity expert, some months ago.
In fact, over two-thirds of all enterprises around the world are planning to pump a minimum of 5% of their IT budgets into shoring up cyber-security defenses through 2020 according to the latest research (PwC research)
For an orchestrated cybersecurity and data protection strategy, that optimises investments (or spending, to some), and diminishes security risk, businesses can put together an information security steering committee. It’s role comprises three major actions: enablement, governance and leadership. More specifically, it has to do with defining clear roles, processes and resources to develop information security, cybersecurity and data security policies, security administration, security operations and control, and awareness and education programmes for employees and, more broadly for all stakeholders and shareholders if necessary.
Admittedly though, these committees may have a hard time aligning business objectives with strategic investment in security matters.
Finding a seat for the CISO
Back in the days prior to when the internet took our lives by surprise, CIOs and CISOs didn’t exist. William Synnott and William Gruber coined the term in the early 80s, in the book, “Information Resource Management: Opportunities and Strategies for the 1980s.”
However, towards the mid-90s, businesses started to foresee the potential of the internet and looked for more strategic ways to apply this new technology. The internet was showing great potential to explore new markets, attract new customers and retain them. This is when the CIO, as we know it, was born.
The BS 7799 standard published by BSI Group in 1995, and 17799 ISO standard by ISO released in December 2000, boosted the CIO presence. The ISO/IEC 27001:2013, reviewed earlier this year, is the current norm that specifies “the requirements for establishing, implementing, maintaining and continually improving an information security management system within the context of the organisation”.
But the coin-has-two-sides life principle didn’t take long to enter the scene. The internet development brought cyber threats that have diversified and become more and more sophisticated since then. This is when the CISO was born.
Tech savvy-only in the beginning, both the CIO and the CISO have long been seated near the backdoor of the board’s meeting room. Nerdy, if the term helps you understand what the perception was, they exclusively dealt with the operational, technology heavy part of information security and cybersecurity, but they weren’t directly involved in strategic decision making.
Things have changed, forced by the evolution of technology and how it has infiltrated our personal and professional lives, sometimes for bad, sometimes for good.
Today’s CIOs and CISOs need, not only a comprehensive knowledge of technology, but a solid business background and leadership skills. Their decisions affect business and risk management, and therefore, revenue streams and brand reputation. Their voice in the board is increasingly imperative.
The CEO doesn’t need to be technically savvy but requires an overall understanding of security and cybersecurity risks and what their impacts are. For CISO and CIO, it’s crucial to have a direct line of communication with the CEO so as to address cyber-related matters more timely and effectively.
CEOs deal with both financial and operational risks. CISOs and CIOs don’t want risks linked to security to become real problems. Both are, ultimately, pushing in the same direction, trying to achieve the same goal.
According to PwC’s GSISS Survey 2018, 27% of CISOs CISOs are now reporting directly to the board. Should and could they work more closely?
Exploring the conflicts between CISOs and CIOs
One may think CISOs and CIOs are normally aligned but, more often than not, they have a conflict of interest. The first one is visibility. There is a common belief that the CISO should report to the CIO, however this is detrimental to CISOs’ access to senior leadership.
The second has to do with the security role in itself. If the CISO works on achieving better, sound cybersecurity, doesn’t its role demand a separation of duties without which a potential CIO’s conflict of interest couldn’t be uncovered?
And the third is risk-related. Information security, the issue CIOs deal with, is a business risk and not only an IT risk.
In Luxembourg, in some companies, the CISO is under the CRO (Chief Risk Officer), the CCO (Chief Compliance Officer) or even the CFO.
CISOs in the IT department
CISOs could also report to the IT department, frequently considered as secondary, an instrument of support rather than a business development unit. The CISO role, as a consequence, is mainly operational – the first line of defence, and its strategic dimension reduces or is, simply, nonexistent.
In other cases, CISOs actions are overseen by an intermediary governing organism, right below the management board in the organisational chart. This indirect, sometimes inefficient and clumsy process doesn’t help achieve the necessary cyber resilience current times call for.
In the future, the CIO and the CISO need to be on the same level as the CEO, so they can deploy a long-term strategy for IT and cybersecurity, respectively.
Befriending the DOP and the CISO
The DPO and the CISO are, somehow, comparable roles, but with slightly different scopes. Whilst the DPO is the custodian of both clients and employees’ personal data, the CISO works on preventing and fighting cyberattacks and data breaches that can affect personal data. The DPO, therefore, supervises the CISO, as the latter is related to personal data too.
In general, the DPO’s positioning in the organisational chart is still fuzzy, recalling, somehow, the CISO’s situation a decade ago or so.
The need for CEOs to evolve their approach to cybersecurity
The “Fear, Uncertainty and Doubt” approach is becoming less fruitful when convincing an executive. They’ve heard already so many horror stories that it doesn’t push them to invest more in cyber. Clearly one needs to accept that prevention is only one part of the game, it might even be impossible to prevent in some cases.
Investing money not only in preventing cyberattacks but also to detect them quickly, in due time, is a much-needed mindset change that CEOs and organisations want to embrace. This requires the skills and capacity to limit damage and unveil the hackers or perpetrators. Many still find this difficult to understand and apprehend. The time to be prepared for the unknown has come. Cyberattacks are becoming more and more sophisticated.
How CEOs can move cybersecurity forward
Here are 6 recommendations for CEOs to upgrade cybersecurity in their organisations:
- Regardless of the industry or business size, some basics need established from the outset. It is paramount to have the right structures in place such as a CISO and steering committees. A CEO wants to guarantee that the CISO can seamlessly access an executive member, or has a seat on the executive committee. This question is relevant to this matter: “Is the CISO in the second line of defence—the one linked to monitoring management and compliance oversight, or is it stuck in between the first and second line of defence (the first has to do with implementing controls and procedures for day-to-day risk management and for supervising their execution”.)
- Engage in awareness and education in cybersecurity, and lead by example. CEOs want to make sure that the security policy is known across the company but also by the board members. Yes, trying to learn the security policy by heart is senseless and virtually impossible, but a 10-commandment approach is highly effective.
- Create a culture were error is allowed so that your users do not hesitate to report an issue. If they try to cover it up, the aftermath will likely be worse.
- Align the IT strategy with the business strategy and incorporate security-related matters from the start, or when rethinking the strategy.
- Avoid departments running their own IT solutions because that translates into a difficult-to-control shadow IT. Successful cybersecurity starts at home and the first rule is to keep the IT environment under control.
- Think of cybersecurity as another business investment to improve the bottom line instead of an expense or burden. Organisations may not clearly realise how dependent they’ve become on technology. As a result, they do not provide a sufficient budget for running it and securing it properly.
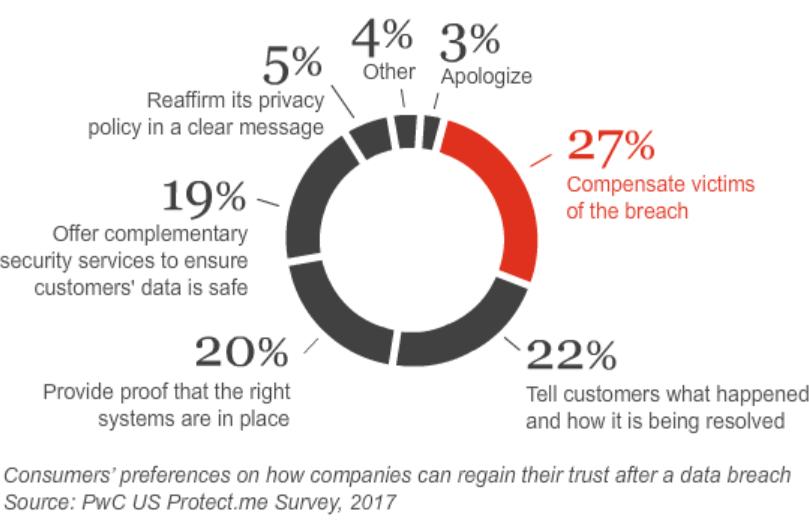
Trust is a business imperative in disruptive times. But, because it’s quickly fading, rebuilding and keeping it is becoming a powerful business differentiator and successful cybersecurity is a central element in the trust equation.
Indeed, one could say that trust is like a silent blockchain that lives in clients’ minds. Cybersecurity is one of the blocks. Business reputation is the virtual currency that help the business stand out.




